CAC Authentication
Secure your website to U.S. Government compliance control standards.
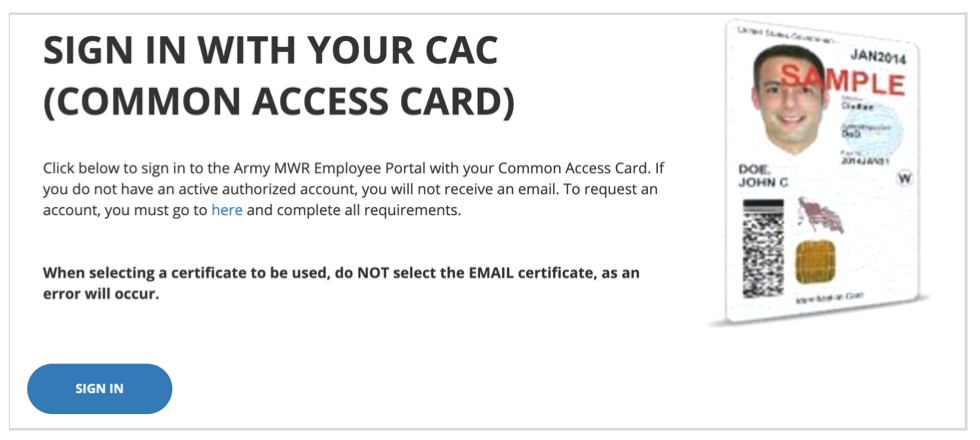
A Single Sign On (SSO) Provider that uses PIV/CAC cards for authentication. It is a stand alone Concrete site itself so it’s easy to run in a similar environment to your other Concrete websites. It centralizes both authentication and authorization for any other Concrete sites you connect to it.
-
Requires CAC cards and joins them to user accounts.
-
Connects to multiple Concrete sites.
-
Allows you to manage who has access to specific sites and groups within those sites from a centralized location.
-
Single installation can power unlimited number of users, unlimited number of connected sites.
-
Can import users from an existing Concrete site.
-
Includes up to 4 hours of consulting time for setup and configuration.
FAQ's
CAC (Common Access Card) authentication is a multi-factor authentication system used primarily by the U.S. Department of Defense (DoD) for secure access to military and government systems. Here's how it works:
-
Card Issuance: A CAC is issued to military personnel, government employees, and contractors. The card contains a microchip with encrypted personal data, including digital certificates for authentication, encryption, and digital signatures.
-
Physical Access: The cardholder inserts the CAC into a card reader connected to a computer or secure access point.
-
Personal Identification Number (PIN): After inserting the card, the user must enter a PIN. This serves as the second factor in the authentication process, combining something the user has (the CAC) with something the user knows (the PIN).
-
Digital Certificates: The microchip on the CAC contains digital certificates that verify the user's identity. These certificates are used to establish secure connections, encrypt emails, and sign documents digitally.
-
Authentication Process: The system reads the card's microchip, verifies the PIN, and uses the digital certificates to authenticate the user's identity. This process ensures that only authorized individuals can access secure systems and information.
-
Network and Application Access: Once authenticated, the user gains access to the network, specific applications, and sensitive data according to their role and permissions.
CAC stands for Common Access Card. It is an identification card issued by the U.S. Department of Defense to military personnel, government employees, and contractors, providing secure access to DoD systems and facilities.
Both CAC and PIV (Personal Identity Verification) cards are smart cards used for secure authentication, but they serve different organizations and have some distinctions:
-
Issuing Authority:
- CAC: Issued by the U.S. Department of Defense.
- PIV: Issued by various U.S. federal government agencies under the guidelines of Homeland Security Presidential Directive 12 (HSPD-12).
-
User Base:
- CAC: Used by military personnel, DoD employees, and contractors.
- PIV: Used by federal employees and contractors across various government agencies.
-
Standards and Compliance:
- CAC: Complies with DoD-specific standards and requirements.
- PIV: Complies with federal government standards set by the National Institute of Standards and Technology (NIST) for secure identity verification across all federal agencies.
-
Functionality:
- Both cards use similar technology for secure authentication, encryption, and digital signatures. However, CAC cards may include additional functionalities tailored to DoD needs, such as specific access controls for military applications.
In the context of security, CAC (Common Access Card) represents a critical component of identity and access management (IAM) within the U.S. Department of Defense. Here's what it means for security:
-
Multi-Factor Authentication (MFA): CAC authentication combines something the user has (the card) with something the user knows (the PIN), enhancing security by requiring multiple forms of verification.
-
Digital Certificates: The CAC contains digital certificates for secure authentication, encryption, and digital signatures, ensuring that communications and transactions are protected from tampering and unauthorized access.
-
Secure Access: By using CACs, the DoD ensures that only authorized personnel can access sensitive systems and information, significantly reducing the risk of unauthorized access and cyber threats.
-
Identity Verification: The CAC provides a reliable means of verifying the identity of military and government personnel, both in physical and digital environments, supporting secure operations and information sharing.
-
Compliance and Standards: The use of CACs ensures compliance with stringent DoD security standards and policies, contributing to the overall security posture of military and government operations.