Small businesses often don't consider customer data policy as their priority. But with 43% of cyber attacks targeting small businesses, one thing is clear: protecting and controlling data is critical.
A few consequences of dreaded breaches include losing your customer’s trust, hefty penalties from your e-commerce platforms such as Google, Pinterest, and content deleted from your CMS. Your website can go from being an authority in your niche to failing to appear in the search results. Imagine all the work you’ve put into creating pillar pages and topic clusters on your blog …. wasted…. due to cybercriminals.
Hackers are attracted to sensitive information and you have to think past just being concerned about banking details, government id numbers, and health care information. Therefore, one of the best ways to keep your business safe from cybercriminals is to have a customer data privacy policy and comply with it.
Here are twelve customer data privacy tips for your business:
1. Know what data you are collecting and where it is!
Sounds obvious. But…the saying is true in this case - common sense is not as common as it should be. How can you protect something if you don’t know that you have it or where it is? How can you tell people you have lost something of theirs if you don’t know where it came from/who it belongs to? How can you know what data regulations your company is responsible to follow if you don’t know where your data came from?
Don’t forget the stuff you used to collect and still have hanging around! Does your company have an approval process in place before more data is allowed to be collected? If yes, does your entire company even know about it? What about logs - is that part of the “approval process”? How are the data backups controlled?
What about your “external parties”....like those easy to use SaaS products someone has purchased with a credit card (with or without your IT department’s knowledge) Are you tracking what data you are sending to them? How are data downloads controlled? Are there spreadsheets full of customer data floating around your company or sent to the customer to float around the customer’s company?
2. Privacy by Design
Make sure that identifying and assessing privacy risks is an integral part of your system/product development life cycle. Ensure that a Privacy Impact Analysis (PIA) is performed whenever a system/product is built, modified or deprecated. It should identify the most current security protocols and require them to be in place to protect the data. It should identify what is allowed to be logged. Your PIA should identify the maximum dataset allowed to be collected. It should identify any new access restrictions that might be required for the data.
Make sure that the PIA includes a review by someone who understands the contracts and Data Processing Addendums your company has signed with your clients. Have you committed to keep a specific client’s data in a specific region? Have you committed to getting a specific client’s permission before bringing on a sub contractor?
Your PIA should include determining if there are any regulations that your company might now have to follow because of the new or modified system/product/service.
3. Only collect essential information
Your customer data privacy policy should specify that you’ll store only the data you need. If you’re not going to use specific information, don’t ask for it.
Security breaches affect businesses regularly. Therefore, it’s critical to distinguish between storing the data you need, like names or addresses, and the data you don’t need, like credit card details.
In most cases, creating a framework that allows third-party processors to handle credit card information is much safer. PayPal, Stripe, and Square are a few examples of trusted payment processing providers. It’s their priority to have strict security procedures to store sensitive information.
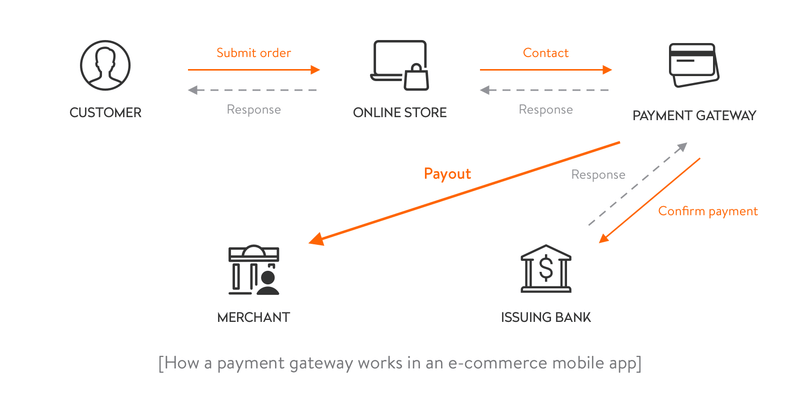
You need to carefully consider all the information you request through the different forms on your website. These forms include payment pages, account creation, newsletter subscriptions, and landing pages.
Let’s say, for example, that you have been running a digital bookstore for a few years. You noticed that you never call your customers on their mobile. As your products are digital, the phone numbers are not needed for the couriers either. There’s no purpose in collecting this information in this case.
Segmenting your database allows for creating effective email marketing. You can group your customers, for example, based on products, contact dates, or their position in the sales funnel. If you can segment your customers based on the sales and behavior information, perhaps you can limit the personal information you collect.
4. Regularly Audit what data you are storing
Do you ever review api parameters, log details, databases, etc to know exactly what is being collected and stored? A company’s database is an essential part of the business. As many users might have permission to work with the data, it is vital to audit it regularly. An audit will let you check if the sensitive customer information has been used correctly.
Moreover, registering the users, time, data, and changes can help businesses comply with many data compliance rules.
In other words, a database audit is an assessment tool that looks at an organization's privacy protection policies and procedures. That is especially important to keep up with constantly changing relevant laws or regulatory requirements.
If you use Windows as your operating system, you can track database administrative activity via Microsoft SQL Server. Microsoft provides an SQL Server Audit tool that reads transaction logs and records information about data and object changes within the database. The tool enables the administrators to investigate any suspicious activities in the databases. It can be used to create server-level audits and database-level audits, with several auditing levels.
5. Have a transparent privacy policy or policies
Your business should have a valid and up-to-date privacy policy that complies with privacy laws in your country and ALSO the countries in which you do business. This policy should be easy to understand and find on the website. Most businesses display the policy in the website's footer and their Contact Details and Terms of Use. Here’s a screenshot of ConcreteCMS.com’ footer showing the location of their Privacy Policy:

If your business is a “data processor” i.e. collects/transmits/stores data on behalf of your customers, then you should ALSO ensure that data is included in a privacy policy.
Some companies have a “legal” as well as a “common language” sections (or even separate versions) of their privacy policy to conform with newer privacy regulations requirements to be understandable. https://www.nytimes.com/interactive/2019/06/12/opinion/facebook-google-privacy-policies.html is a great article which discusses how any Privacy Policies have become exceedingly more arcane over time requiring graduate level vocabulary to be comprehensible. Your privacy policy should explain your company's online information practices and your customer's choices about how their information is collected and used. For example, it should tell your customers how their data is protected and stored and who handles it. The more detailed information you give, the better.
You should also include the following in a privacy policy:
- Who do you share the data with
- Data security providers you use
- Technology you use
- The level of encryption used
- The type of cloud or physical storage used
- The steps your company takes in the event of a breach
Give your customers a chance to ask questions, make comments, or complain about compliance with your privacy policy. In many countries, you are obliged to delete customer data when they request it. Let them know that they are free to contact the company in case of any concerns.
If you do business in the US and the EU, mention in your Privacy Policy that JAMS can be used for dispute resolution https://www.jamsadr.com
If your company is walking the walk of your privacy policy, then you should not have to worry about a flood of complaining customers.
6. Encrypt stored and transmitted data
Encryption means encoding the data so people cannot read it without inputting a password. Encryption software uses complex algorithms that take plain text and scramble it into an unreadable format. The party wanting to unscramble the received information must use a password to decrypt the message.
Only 22% of small businesses encrypt their databases. That is surprising as encrypted information has a lower chance of becoming a target for criminals.
Encryption allows for protecting data stored on your computers, servers, and networks. You can encrypt individual files, folders, entire disks on your PC, and USB flash drives and files stored in the cloud. Most devices allow an administrator to configure encryption and set a password easily.
Encrypting data at the collection point is just as important as encrypting it when it’s stored. Use services like Let’s Encrypt to generate HTTPS certificates for your website. HTTPS is an internet communication protocol that protects the integrity and confidentiality of data between the user's device and the website.
Does your business do an annual review of its cryptographic policies to make sure that it is following industry standard best practices? Do your certificates have key sizes greater than or equal to 2048 bits? Are you transmitting ALL data using TLS 1.2 or above or is your business using a compromised protocol? Are the cost factors for your password hashing algorithms you are using robust enough to withstand modern attacks? Do your ciphers have key sizes greater than or equal to 256 bits?
The customer data you collect at the order checkout must be adequately encrypted during transmission. Any stored payment information has to be protected and hosted securely. The data could be self-hosted on your store’s servers or hosted by your payment provider.
Encrypting emails can lower the chances of a hacker accessing information from your emails. Different Gmail add-ons, like FlowCrypt Gmail Encryption or DocuSign, allow additional encryption on emails and documents. While email providers usually have their encryption as a standard, using additional security tools will add another layer of protection.
Remember that if your data is lost or stolen, people won’t be able to read it if it’s encrypted.
7. Keep your software updated
Keep your employees and contractors' devices updated.
Keeping your software updated on all devices is one of the easiest ways to protect your business from cyber threats. If you protect your devices, you protect your business.
Hackers are constantly changing their methods of stealing information. To stay on top of threats, software manufacturers offer regular updates. These updates include software patches to security holes that have been discovered. Software patches cover the security holes to keep your data secure from hackers.
Businesses often leave updating to quieter periods. That is a mistake. If you don’t update or leave updating for too long, your business can become vulnerable to losing sensitive information.
Let updating your software become a routine. If you do it every business day, it will become a habit. Educate your employees on the importance of software updates. Your employees help keep your business secure. Even better, centrally control your company’s machines and push updates to them.
Keep your servers updated
Subscribe to services like US-Cert and apply the latest patches to protect your business against software vulnerabilities and known exploits. Many people rely on their cloud providers and SaaS solution providers to keep them up to date….but it is rarely that cut and dry. Make sure you know exactly what your responsibilities are and what their responsibilities are as your Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and/or Software as a Service (SaaS). Learn specifically what you are responsible to keep up to date.
8. Keep your customers informed about any customer data policy changes
Customers are usually not too keen on sharing their personal information with brands. The main reason is not knowing what will happen with the information. For that reason, your company should be transparent with the customers about any changes to your customer data policy.
In many cases, customer data privacy requires you to inform the customers how you use the data anyway. You may, for example, need to share their contact details with couriers’ VoIP phone services for purchase to take place. So, if you're changing the courier service, let your customers know by explaining how this will affect the handling of their personal information.
If you’re writing an email or a Facebook post regarding your clients’ data handling, try to keep it brief, and on point, don’t include any sales links, and avoid the use of buzzwords. The message is supposed to inform, not to sell.
For example, Panasonic sent the email below when the company changed its privacy policy:
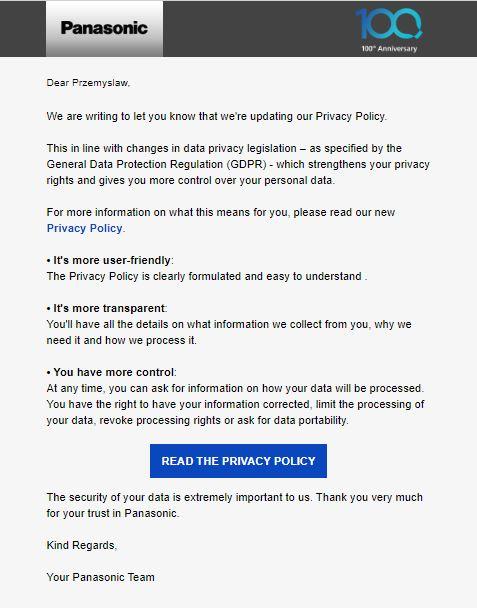
Keep your customers informed on how you use the data at all times. By being transparent, you will earn your client’s trust.
9. Limit data access
The fewer people have access to the data, the better. This is the “Principle of Least Privilege” Your data policy privacy should define who has access to data.
To keep the risk of losing your customers' sensitive data to a minimum, make sure that only approved team members have access to sensitive data. You should perform access reviews regularly. You should have a process to add new systems collecting data to a Systems List and flesh out the Access by Role as the new system is adopted. Who is going to be the system owner and be allowed to make changes to the Access by Role for that system?
10. Train Your Team
You should train employees with data access in sensitive data handling. They should be able to spot risks.
If you are collecting analytics, make sure that your team knows the difference between anonymization and pseudonymisation.
Make sure all of your staff know your company's customer data privacy policy. You should teach your employees how to handle sensitive information. Have specific guidelines so that they can carefully follow every step to ensure the data is not exposed.
Educate your employees on recognizing phishing attacks and data security best practices. Hackers get smarter every year, so regular cyber security awareness training should also be mandated at any company.
11. Regularly test your data systems
Testing your data security systems once or twice a year is a minimum recommendation to keep the data held by your company secure.
If you run an eCommerce website, cybercriminals will target your business. The type of sensitive data being exchanged is a lure.
To protect your eCommerce, consider penetration testing. Penetration testing helps to identify your system vulnerabilities. The testing is oriented towards eCommerce functional modules and can help identify issues specific to the website’s design, mobile payments, and integrations with third-party platforms.
The most important thing to remember from this point is that if you miss finding your business’s weak points, someone else will. And, common sense…. Fix what you find!
12. Prevent security risks in mobile devices
Mobile devices such as smartphones, tablets, and laptops add extra flexibility for a user. They can be a source of additional risk. If someone loses a mobile device, other parties will have access to sensitive information, and this exposure can harm your business or clients.
To protect your customer data privacy, stress the importance of keeping mobile devices secure among your employees. Ensure everyone is aware that it’s critical to report a theft or loss as soon as possible after the incident so that the company can react and implement protective measures on the data before any data breach.
Have controls for securing mobile devices. Have guidelines for what company systems/services specific types of mobile devices are allowed to connect to. Common controls include requiring a VPN for connectivity, PKI encryption to production, non-mobile-device related multi factor authenticator (such as Yubikey), and implementing a tool to control what is allowed to be present on a device (something like Kandji, MaaS 360)
Summary
Getting customer data privacy right for your business can only bring positive results. Even if there isn’t specific legislation requiring their data to be handled in a specific way, customers expect their information to be handled safely and be used only for the reason they entrusted it to you.
The top tips for customer data privacy for your business include:
- Collecting only the essential information.
- Having an honest privacy policy.
- Keep your customers informed.
- Limit your database access and audit it regularly.
- Encrypt the data stored.
- Keep the software updated.
- Regularly test your data systems.
Lastly, make sure you prevent security risks in mobile devices in case of a loss or theft of a device.
Keep yourself and your employees educated and your customers informed to avoid being an easy target for cybercriminals. When customers give your details to you, they trust you. So, make sure you do everything you can to ensure that the data does not get into the wrong hands.
David Campbell is a digital marketing specialist at Ramp Ventures. He helps manage the content marketing team at Right Inbox. When he's not working, he enjoys traveling and trying to learn Spanish.
