Who doesn’t have remote employees now? Did you onboard anyone in Covid who has never met anyone else in person in your company? Remote workers can’t just walk down the office hall to Bob’s desk and ask “How am I supposed to do W?”, “Where do I find X?”, “Who is the best person to ask about Y?” Bob, the knowledge expert at your company, might be a teleworker and those that are physically in the office might not know that he is the physical manifestation of your company’s Google search engine. Hence, having an intranet, or HR Hub, has become a vital resource in these post-covid days so that your employees across different departments can gain access to applications, official documents, and essential information no matter where they are.
Many organizations think of “marketing”, “communications” or “HR” applications like your intranet as “non production” systems that do not need to be protected. They forget, or more likely don’t even realize, that intranets can be gateways into your organization.
Since it contains so much sensitive information (proprietary information, intellectual property, employee PII, Customer Information, etc) a data breach affecting your intranet would be a disaster! So, what can you do to ensure that your intranet is as secure as possible?
Work With HR, Legal And IT For Better Cohesion
Don’t roll out a new intranet without buy-in from everyone. Different departments each have their own way of communicating and will need to be convinced that having a standardized intranet will be beneficial for everyone. It is important to understand the roles of different departments in building a secure intranet. You will need to collaborate across the entire company.
If you are bringing in new software for your intranet, make sure that you get the appropriate approvals and risk assessments done per your company’s rules. You also need to collaborate with HR and Legal to ensure that sensitive information contained in, or obtained by, your intranet is handled correctly and you don’t face lawsuits.
Are you going to have to lean on IT to set up the technical side of the intranet, its login systems, and the way data is managed? Will Engineering or Operations need to spin up and maintain a server? Then you need to make sure that they are on-board with it. You will need to discover if they have the required expertise to keep the software your intranet depends on up to date (your Content Management System (CMS), your webserver, the server-side programming language used etc).
Host Your Intranet In A Secure Environment
The first consideration for your secure intranet is where you are going to host it.
If you are hosting your intranet yourself, make sure it is included in your security program!
Perhaps hosting your intranet yourself, whether on premises or in your company’s cloud, is a daunting and bewildering responsibility. Perhaps the department in your organization with the expertise to build and maintain it either can’t, or won’t, take on the additional work and you need to pass the responsibility to keep the infrastructure secure to someone else.
Make sure you look for a host which provides industry standard security controls and make sure that the hosting provider themselves has had an independent external audit of those controls. Don’t accept your hosting provider passing off 3d party certifications (such as AWSs) as the hosting provider’s own security program. If you see the words “we store our data in
Also, make sure that your intranet is in scope for the Hosting Provider’s aforementioned compliance and not hosted in a legacy environment.
Specific security and privacy certification and compliance reports let you know exactly what controls your hosting environment has in place. That’s a topic for a whole other blog but you can assume that adequate security controls are in place if your hosting environment is one of PCI, ISO 27001/27018, HITRUST, FedRAMP or StateRAMP certified and/or can give you a current (within 12 months) SOC 2 Report.
The other plus of having your intranet hosted by a hosting provider who will provide you with valid SOC reports is that your organization can inherit, aka “carve out”, your hosting provider’s compliance for the Intranet Hosting should you need SOC 2 compliance for your entire organization. Ditto for other compliance frameworks.
Know What YOU Have to Do
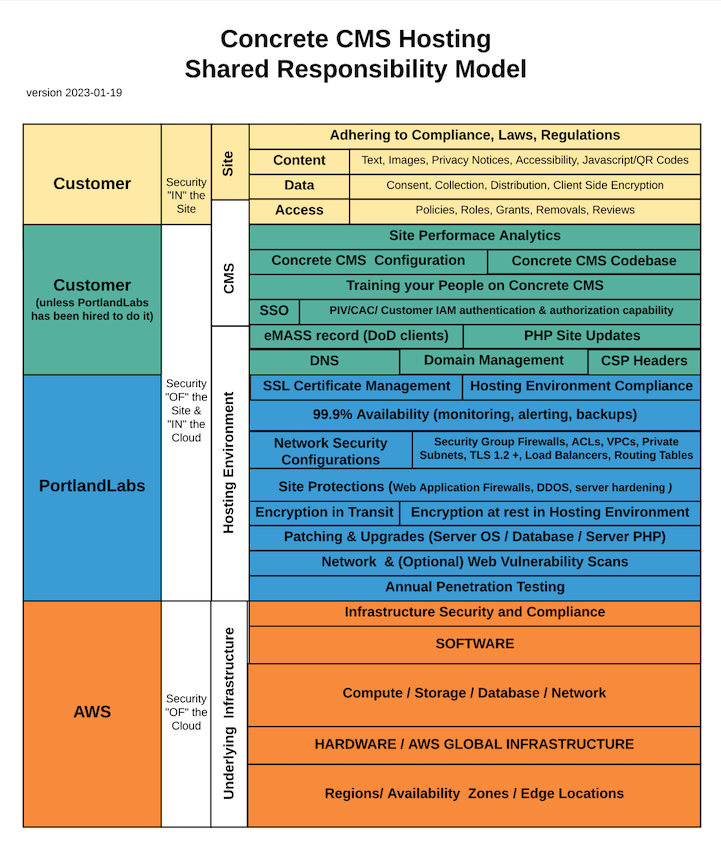
Know exactly what your Hosting Provider does and what you are expected to do to keep your intranet safe. A good hosting provider can give you a detailed Shared Hosting Responsibility Matrix.
Your hosting provider should also have a standard Data Processing Addendum that you should both sign which lays out technical data processing requirements. It should include terms about how data is stored, protected, processed, accessed, and used. The agreement should also restrict what your hosting provider can and cannot do with your data.
Basic Site Security Protections
An intranet is basically a private website that a user needs to log in to see. Hence, all the same protections you give your public website should also be set up for your intranet.
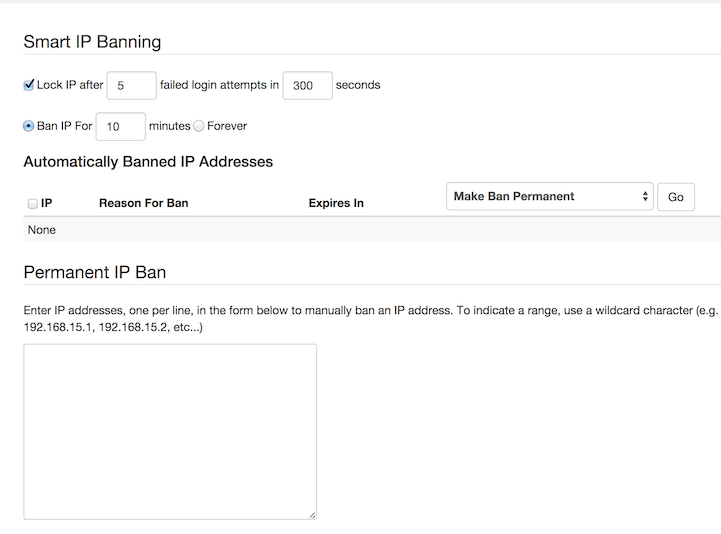
- Put Firewalls in Place
- Use Security Headers
- Use modern, strong, authentication protocols such as SAML, OAuth2, OpenID, and OpenID Connect
- Enforce strong passwords
- Enforce Multi Factor Authentication
- Hash passwords
- Redirect all HTTP traffic to HTTPS
- Use TLS 1.2 or greater security protocols. Disable Secure Socket Layer SSL2 and SSL3
- Ensure all ciphers have key sizes greater than or equal to 256 bits and all certificates have key sizes greater than or equal to 2048 bits
- Implement HTTP strict transport security (HSTS)
- Configure to use approved publicly trusted server authentication certificates.
- Disable DES, 3DES RC4, NULL and export cipher suites
- Enable DNSSEC
- Monitor incoming traffic, set alerting rules, and alert 24 x 7
- Encrypt data in transit and in storage
Protect your Intranet behind a VPN, a CASB, or an Enterprise Browser
Since your intranet is private, you can also add in additional security controls that you can’t for a public site.
VPN
Your company may have a virtual private network (VPN) that employees can use to more securely manage their connection. Requiring intranet users to be on a VPN to access your Intranet is an easy way to add a strong level of security to your ecosystem. You could also allow-list specific IP addresses permitted to access your content. However, that restricts employees to working in only specific locations which wouldn’t jive with the current “work wherever” culture.
CASB
Another option is a Cloud Access Security Broker (CASB) which extends the security perimeter outside of the “corporate network”. A CASB enables organizations to apply security controls to cloud applications, like your intranet, regardless of where they are hosted and regardless of where the users access them.
CASBs can detect and respond to threats in real-time and so can mitigate potential risks before they cause any damage. A CASB can monitor data at rest, in transit, and in use within the intranet, and apply encryption, data loss prevention (DLP), and other security measures to protect the sensitive data in your intranet.
Enterprise Browser
Enterprise Browsers, like Island’s, are new to the scene and offer a more streamlined way of managing privileged access. Since Enterprise Browsers are centrally managed by the organization, administrators can add a layer of visibility and control to any admin interaction from inside the browser itself, without writing a line of code. With an enterprise browser, you can add an approval step for sensitive application actions, insert an extra layer of authentication before accessing the intranet, audit and log all activity within a browser session, and share that data with existing analytics platforms for the complete picture of all privileged user activity.
Administrators can deploy and manage the browser settings across all networks, locations, and devices that access the intranet. You can configure it to allow users to log into your intranet only from your organization’s Enterprise Browser. You can customize it to disallow downloading, copy/pasting, saving, or printing specific content. It can even be used to prevent screenshots from being taken! By putting organizations control over the “last mile”, enterprise browsers offer more visibility, governance, and highly particularized protections over your intranet while dramatically simplifying the management and cost overhead of doing so.
Configure your Intranet CMS Correctly
Whatever content management system you are using for your Intranet, ensure that you are following that system’s Configuration Best Practices so that you don’t accidentally create “holes” bad actors can use to attack your organization.
Ensure There Are Appropriate Log-in Requirements
As the recent Lastpass breach demonstrated, multi- factor authentication (MFA) is vital if you’ve got more sensitive content to protect.
Having your Intranet login tied to your organization’s Identity and Access Management system (IAM) for centralized access control is also a good idea. Not only does it increase security but the users of your Intranet would also appreciate the ease of entry if you set up Single Sign On (SSO). Hence, make sure that whatever intranet system you choose works well with standardized authentication protocols such as SAML and LDAP.
A good SSO provider can be configured to occasionally require MFA login, but not require it every time the user is visiting the site. Be deliberate about setting the number of days between re-authentications.
Some organizations require physical MFA devices like a Corporate badge, Government PIV/CAC, or yubikey. BASF uses Single Sign On (SSO) with employee authentication cards protecting access to their Intranet which is hosted by the team that built and manages Concrete CMS and is kept secure through an ongoing maintenance and support agreement.
When thinking about how people log into the intranet, you also need to consider how they log out. A good starting point is to implement an automated system that logs people off after a period of inactivity. However, you should always have a logout button as this encourages personal responsibility and is important if someone is using a shared machine. Some organizations go as far as deleting a user’s access if they have not used a system in a set period of time.
Granular Control of Different Areas of Your Intranet
Gating Viewing Content
You should consider if you really want every employee to be able to be able to access all the information on your intranet or if it would be handy to have A hierarchy of access and permissions. Work on a means of restricting access to sensitive information where necessary and develop scope based granular access based on the type of information and department.
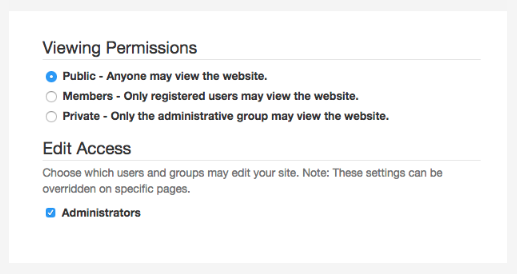
Concrete CMS lets you set different parts of your site to be accessible to different user groups, and by default new pages created in those areas will follow those permissions.
In addition, you can configure certain types of pages to always be managed with a different permission set. For example, you can combine these approaches to have private areas for different departments, but still maintain the ability for the PR department to write a press release that shows up anywhere.
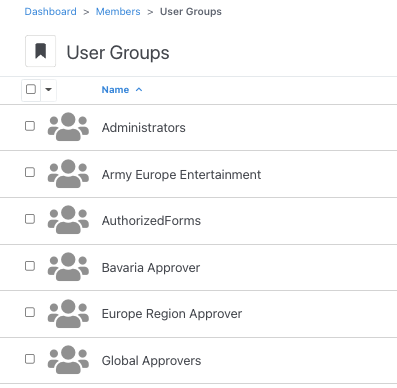
Concrete CMS can also be easily configured to create custom user groups specific to your organization’s needs.
Concrete CMS lets you set different parts of your site to be accessible to different user groups, and by default new pages created in those areas will follow those permissions.
In addition, you can configure certain types of pages to always be managed with a different permission set. For example, you can combine these approaches to have private areas for different departments, but still maintain the ability for the PR department to write a press release that shows up anywhere.
Concrete CMS can also be easily configured to create custom user groups specific to your organization’s needs.
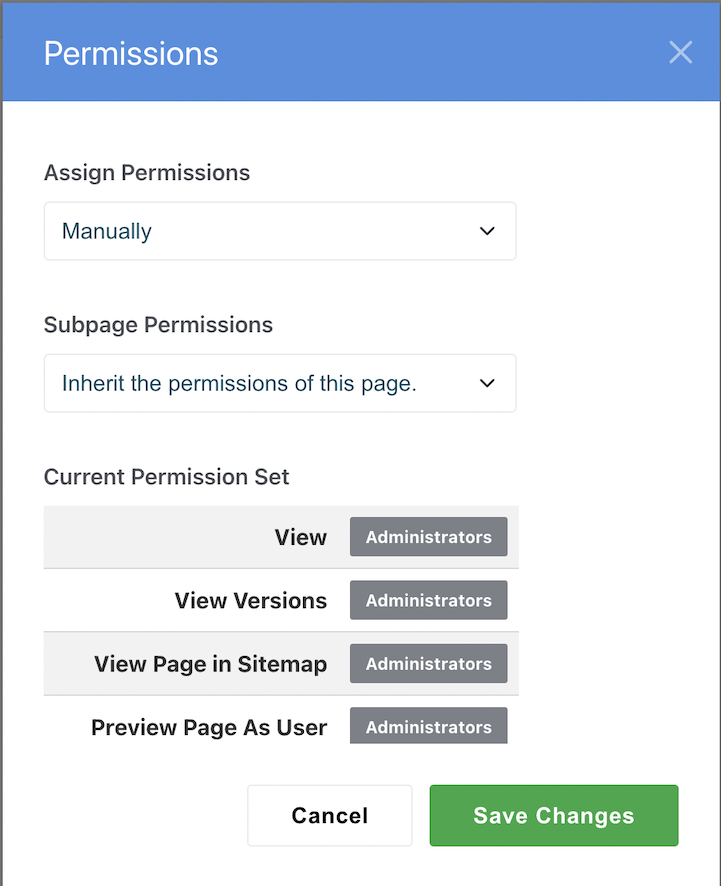
Gating Creating & Editing Content
If you don’t want to do all the work yourself to keep every page of your intranet current, then choose an Intranet system which allows granular permissions to edit specific areas and pages of your intranet. Concrete CMS allows you to grant permissions directly to an individual or a role which you can create. Workflows can be set up if approvals are required before content can go live.
Delegating content maintenance to trusted individuals in different departments by using granular permissions to different Intranet areas or pages will help ensure that your Intranet stays fresh. An Intranet that is kept current is used; a stale Intranet is not.
Establish Clear Protocols And Training For All Users
While this hierarchy system of access is effective, it pays to create a strong company-wide protocol where all employees have a clear understanding of the importance of protecting the data on the intranet. This means ensuring they know what they can and can’t do with specific data. An Enterprise Browser can be configured to prevent data loss by doing things such as restricting downloads and preventing screenshots.
Update And Review The System Often
Just as you need to audit your content to ensure that it is all relevant and accurate, you will need to ensure that your intranet software and infrastructure is kept up to date. Be aware of published vulnerabilities in the software you use and take action; hackers certainly do! Sign up for alerts from CISA.
It is vital to keep your CMS ( such as Concrete, Drupal, Wordpress, Joomla etc), webserver (such as nginx or Apache), operational software (such as PHP), and underlying operating system (such as Unix, Linux, or Windows Server) updated with the latest patches. Don’t just assume that your hosting provider does this for you - verify!
Make a Commitment Today to Build A More Secure Intranet
As remote work becomes ever more prevalent, your intranet is the veins and arteries transmitting the life sustaining information making your company thrive. Protect it!
Host your intranet in a secure environment and ensure cutting edge site protections are in place. Know what your Hosting Provider patches and what you are responsible for to keep it up to date. Consider using a VPN, CASB or Enterprise browser for added protection.
Rethink how your employees access your Intranet and put granular content management controls in place. Follow security best practice and ensure there are regular reviews to keep both the content and the system current.
